Datasheet 搜索 > 微控制器 > Microchip(微芯) > DSPIC33FJ128GP802-I/MM 数据手册 > DSPIC33FJ128GP802-I/MM 开发手册 1/18 页

 器件3D模型
器件3D模型¥ 47.24
DSPIC33FJ128GP802-I/MM 开发手册 - Microchip(微芯)
制造商:
Microchip(微芯)
分类:
微控制器
封装:
QFN-28
描述:
MICROCHIP DSPIC33FJ128GP802-I/MM 芯片, 数字信号控制器, 16位128K闪存, 40MIPS
Pictures:
3D模型
符号图
焊盘图
引脚图
产品图
DSPIC33FJ128GP802-I/MM数据手册
Page:
of 18 Go
若手册格式错乱,请下载阅览PDF原文件

© 2006 Microchip Technology Inc. DS01044A-page 1
AN1044
INTRODUCTION
Currently, there are three data encryption standards
approved for use in the Federal Information Processing
Standards (FIPS). This application note discusses the
implementation of two of these for PIC24 and
dsPIC30/33 devices: Triple Data Encryption Standard
(TDES) and Advanced Encryption Standard (AES).
TDES ENCRYPTION
Background
The original Data Encryption Standard (DES), a 64-bit
block cipher, was invented in the early 1970s by IBM
®
.
DES uses a 64-bit encryption key: 56 bits for encoding
and decoding, the remainder for parity. It was adopted
by the United States government in 1977 as standard
for encrypting sensitive data. By the mid 1990s, several
public organizations had demonstrated that they were
able to crack a DES code within days.
Triple DES (TDES) is a variant of DES, and is
described in FIPS 46-2 and 46-3. TDES uses three
cycles of DES to extend the key from 56 bits to 112 or
168 bits, depending on the mode of operation. Because
of known weaknesses in the DES algorithm, the actual
security is believed to be on the order of 80 and
112 bits, respectively, for the two different methods.
The use of TDES was suggested by the American gov-
ernment in 1999 for use in all systems, except in legacy
systems, where only DES was available.
There are several different modes of TDES. The most
common involves using two different keys. The data is
encrypted with the first key. That result is then
decrypted with the second key. The data is then finally
encrypted once again with the first key. Other modes of
operation include using three different keys, one for
each of the stages, and encrypting in all rounds instead
of decrypting during the second round. For most new
applications, TDES has been replaced with Advanced
Encryption Standard (AES). AES provides a slightly
higher security level than TDES and is much faster and
smaller in implementation than TDES.
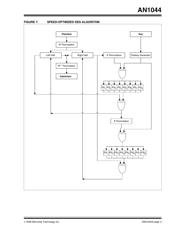
The original DES algorithm is outlined in Figure 1. The
cycle is run 32 times before the ciphertext is valid.
FIGURE 1: ORIGINAL DES ALGORITHM
Authors: David Flowers and
Howard Henry Schlunder
Microchip Technology Inc.
Right Half
Left Half
E Permutation
Subkey Generator
Plaintext Key
S
8
S
1
S
2
S
3
S
4
S
5
S
6
S
7
P Permutation
Old Left
IP
-1
Permutation
Ciphertext
IP Permutation
Data Encryption Routines for PIC24 and dsPIC
®
Devices
器件 Datasheet 文档搜索
AiEMA 数据库涵盖高达 72,405,303 个元件的数据手册,每天更新 5,000 多个 PDF 文件